Authorization Guide
This guide shows you how to get a user’s authorization to access private data through the Web API.
Introduction
All the Yuvo API require authorization; that is, the company admin must have granted permission for an application to access the requested data. To prove that the company admin has granted permission, the request header sent by the application must include a valid access token.
As the first step towards authorization, you will need to register your application. That will give you a unique client ID and client secret key to use in the authorization flows.
Supported Authorization Flows
The Yuvo API currently supports two authorization flows:
- The Client Credentials flow allows you to
get an access token by supplying your client credentials (client ID and secret key). This flow is
used in server-to-server authentication.
Note: With this access token you can create companies and push employee's data from your application. You get full update access to these companies data.
You are responsible for obtaining authorization from your application's users before using this API. Access to any other company (already existing on Yuvo platform) data could only be done via Authorization Code
- The Authorization Code flow first gets a
code then exchanges it for an access token and a refresh token once authorization has been granted by a company admin user. This token gives only access to that particular company data.
Since the exchange uses your client secret key, you should make that request server-side to keep the integrity of the key. An advantage of this flow is that you can use refresh tokens to extend the validity of the access token.
Note: This flow is only necessary for accessing Yuvo data not created by your application via Client Credentials. You will use this flow when an existing Yuvo account company admin will subscribe to your application and give it access to their existing Yuvo data.
Client Credentials Flow
The method authenticates your application requests to the Yuvo API. It gives you full create/update access to Yuvo companies data that were originally sent by your application. This flow is described in RFC-6749.
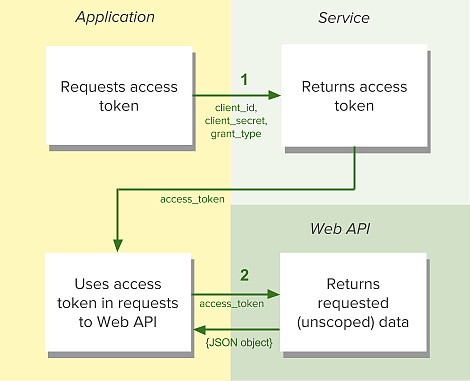
1. Your application requests authorization
The request is sent to the /api/token endpoint of the Accounts service:
POST https://api.yuvohub.com/oauth/token/
The request will include parameters in the request body:
| Request body parameter |
Value |
|---|---|
| grant_type |
Required. Set it to “client_credentials”. |
The header of this POST request must contain the following parameter:
| Header parameter |
Value |
|---|---|
| Authorization |
Required. Base 64 encoded string that contains the client ID and
client secret key. The field must have the format: Authorization: Basic <base64
encoded client_id:client_secret> |
For example:
curl -H "Authorization: Basic ZjM4ZjAw...WY0MzE=" -d grant_type=client_credentials https://api.yuvohub.com/oauth/token/
{
"access_token": "NgCXRKc...MzYjw",
"token_type": "bearer",
"expires_in": 3600,
}
2. Use the access token to access the Yuvo API
The access token allows you to make requests to the Yuvo API endpoints that do not require user authorization.
Authorization Code Flow
This method is suitable for long-running applications which the user logs into once. It provides an access token that can be refreshed. Since the token exchange involves sending your secret key, this should happen on a secure location, like a backend service, not from a client like a browser or mobile apps. This flow is described in RFC-6749.
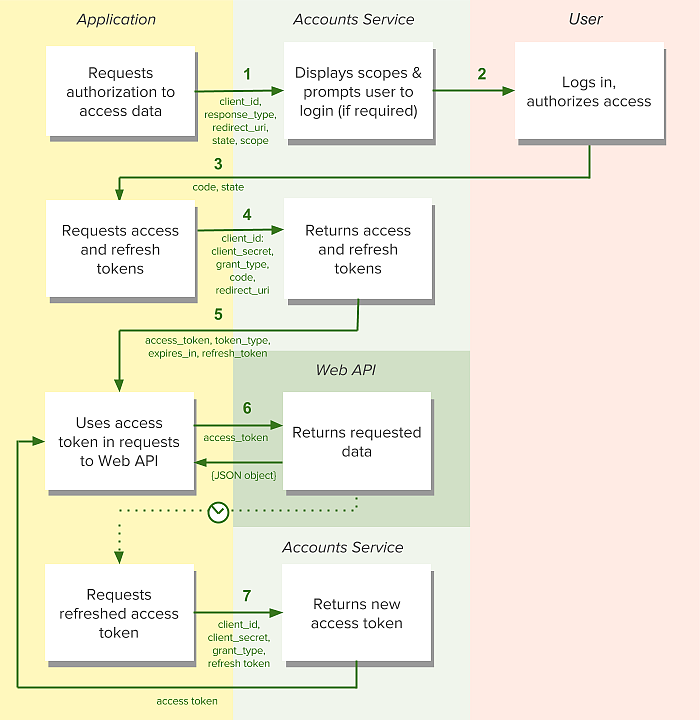
1. Your application requests authorization
The authorization process starts with your application sending a request to the Yuvo OAuth Service.
(The reason your application sends this request can vary: it may be a step in the initialization of your
application or in response to some user action, like a button click.) The request is sent to the /authorize
endpoint of the Accounts service:
GET https://api.yuvohub.com/oauth/authorize/
The request will include parameters in the query string:
| Query parameter |
Value |
|---|---|
| client_id |
Required. The client ID provided to you by Yuvo when you register
your application. |
| response_type |
Required. Set it to code. |
| redirect_uri |
Required. The URI to redirect to after the user grants/denies
permission. This URI needs to have been entered in the Redirect URI whitelist that you
specified when you registered your application. The value of redirect_uri here
must exactly match one of the values you entered when you registered your
application, including upper/lowercase, terminating slashes, etc. |
| state |
Optional, but strongly recommended. The state can be useful for
correlating requests and responses. Because your redirect_uri can be guessed,
using a state value can increase your assurance that an incoming connection is the result of
an authentication request. If you generate a random string or encode the hash of some client
state (e.g., a cookie) in this state variable, you can validate the response to additionally
ensure that the request and response originated in the same browser. This provides
protection against attacks such as cross-site request forgery. See RFC-6749. |
A typical request looks like this:
GET https://api.yuvohub.com/oauth/authorize/?client_id=5fe01282e44241328a84e7c5cc169165&response_type=code&redirect_uri=https%3A%2F%2Fexample.com%2Fcallback&state=34fFs29kd09
2. The user is asked to authorize access within the scopes
The Yuvo OAuth service presents details of the scopes for which access is being sought. If the user is not logged in, they are prompted to do so using their Yuvo credentials.
When the user is logged in, they are asked to authorize access to the data sets defined in the scopes.
3. The user is redirected back to your specified URI
After the user accepts (or denies) your request, the Yuvo OAuth service redirects back to the
redirect_uri. For our example, this would be the address:
https://developers.yuvohub.com/callback/
If the user has accepted your request, the response query string contains the following parameters:
| Query parameter |
Value |
|---|---|
| code |
An authorization code that can be exchanged for an access token. |
| state |
The value of the state parameter supplied in the request. |
For example:
https://developers.yuvohub.com/callback/?code=NApCCg..BkWtQ&state=profile%2Factivity
If the user has not accepted your request or an error has occurred, the response query string contains the following parameters:
| Query parameter |
Value |
|---|---|
| error |
The reason authorization failed, for example: “access_denied” |
| state |
The value of the state parameter supplied in the request. |
For example:
https://developers.yuvohub.com/callback/?error=access_denied&state=STATE
4. Your application requests refresh and access tokens
When the authorization code has been received, you will need to exchange it with an access token by
making a POST request to the Yuvo OAuth Service, this time to its /api/token
endpoint:
POST https://api.yuvohub.com/oauth/token/
The body of this POST request must contain the following parameters:
| Request body parameter |
Value |
|---|---|
| grant_type |
Required. As defined in the OAuth 2.0 specification, this field must
contain the value "authorization_code". |
| code |
Required. The authorization code returned from the initial request
to the Account's /authorize endpoint. |
| redirect_uri |
Required. This parameter is used for validation only (there is no
actual redirection). The value of this parameter must exactly match the value of
redirect_uri supplied when requesting the authorization code. |
| Header parameter |
Value |
|---|---|
| Authorization |
Required. Base 64 encoded string that contains the client ID and
client secret key. The field must have the format: Authorization: Basic <base64
encoded client_id:client_secret> |
An alternative way of sending the client id and secret is as request parameters (client_id
and client_secret) in the POST body, instead of sending them base64-encoded in the header.
5. The tokens are returned to your application
On success, the response from the Yuvo OAuth Service has the status code 200 OK in the
response header, and the following JSON data in the response body:
| Key |
Value type | Value description |
|---|---|---|
| access_token |
string | An access token that can be provided in subsequent calls, for example to
Yuvo API services. |
| token_type |
string | How the access token may be used: always "Bearer". |
| expires_in |
int | The time period (in seconds) for which the access token is valid. |
| refresh_token |
string | A token that can be sent to the Yuvo OAuth Service in place of an
authorization code. (When the access code expires, send a POST request to the Accounts
service /api/token endpoint, but use this code in place of an authorization
code. A new access token will be returned. A new refresh token might be returned too.) |
An example cURL request and response from the
token endpoint will look something like this:
curl -H "Authorization: Basic ZjM...zE=" -d grant_type=authorization_code -d code=MQCbtKe...44KN -d redirect_uri=https%3A%2F%2Fwww.foo.com%2Fauth https://api.yuvohub.com/oauth/token/
{
"access_token": "NgCXRK...MzYjw",
"token_type": "Bearer",
"scope": "user-read-private user-read-email",
"expires_in": 3600,
"refresh_token": "NgAagA...Um_SHo"
}
6. Use the access token to access the Yuvo API
The access token allows you to make requests to the Yuvo API on a behalf of a user, for example:
curl -H "Authorization: Bearer NgCXRK...MzYjw" https://api.yuvohub.com/companies
{
"name": ...,
"uen_code": ...,
"sector": ...,
"entity_type": ...,
"entity_sub_type": ...,
"work_locations": ...,
"departments": ...,
}
7. Requesting access token from refresh token
Access tokens are deliberately set to expire after a short time, after which new tokens may be granted by supplying the refresh token originally obtained during the authorization code exchange.
The request is sent to the token endpoint of the Yuvo OAuth Service:
POST https://api.yuvohub.com/oauth/token/
The body of this POST request must contain the following parameters:
| Request body parameter | Value |
|---|---|
| grant_type |
Required. Set it to “refresh_token”. |
| refresh_token |
Required. The refresh token returned from the authorization code
exchange. |
The header of this POST request must contain the following parameter:
| Header parameter |
Value |
|---|---|
| Authorization |
Required. Base 64 encoded string that contains the client ID and
client secret key. The field must have the format: Authorization: Basic <base64
encoded client_id:client_secret> |
For example:
curl -H "Authorization: Basic ZjM4Zj...Y0MzE=" -d grant_type=refresh_token -d refresh_token=NgAagA...NUm_SHo https://api.yuvohub.com/oauth/token/
{
"access_token": "NgA6ZcYI...ixn8bUQ",
"token_type": "Bearer",
"scope": "user-read-private user-read-email",
"expires_in": 3600
}